Best Vulnerability Management Tools
Best vulnerability management tools are Vulnerability Manager Plus, Qualys Enterprise, AppTrana, Beyond trust, Flexera SaaS Manager, and Nessus. Absolutely visibility of the business networks and accurate reports on the vulnerabilities explain why these tools are so popular.



No Cost Personal Advisor
List of 20 Best Vulnerability Management Tools
Emergents | 2024
All-in-One Vulnerability Management Tool
Vulnerability Manager Plus is a dependable vulnerability management system. It comprises a multi-OS vulnerability management that is integrated with built-in remediation. It enables users to audit out-of-date software, firewall, and antivirus conditions. With the help of an in-built integrated console, IT administrators and security teams can easily execute vulnerability assessments. Learn more about Vulnerability Manager Plus
Explore various Vulnerability Manager Plus features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
- Policy Management
- Vulnerability Scanning
- Vulnerability Assessment
- Vulnerability Protection
- Prioritization
- Network Scanning
- Risk Management
- Web Scanning
Vulnerability Manager Plus Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Emergents | 2024
Tools by Qualys
Qualys offers a reliable vulnerability management solution. It finds vulnerabilities in all networked assets, and peripherals. Any device that has an IP address can be evaluated by Qualys. A platform of integrated solutions, the Qualys Cloud Platform offers enterprises threat protection, asset detection, web application security, network security, and compliance monitoring. Learn more about Qualys Enterprise
Explore various Qualys Enterprise features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Features
View all Qualys Enterprise Features- HIPAA Compliance
- Sarbanes-Oxley Compliance
Qualys Enterprise Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Emergents | 2024
Tools by Rapid7
InsightVM is a vulnerability management software that aids in giving visibility into the dangers in the IT environment. It gives automation, and integration features that businesses need to identify those vulnerabilities effectively. Businesses can view risks from their dashboard in real-time. They can track and share the program's progress toward its objectives. Learn more about InsightVM
Explore various InsightVM features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Features
View all InsightVM Features- Risk Management
- Prioritization
- Vulnerability Assessment
- Patch Management
- Asset Discovery
- Policy Management
- Asset Tagging
- Network Scanning
InsightVM Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Emergents | 2024
Next-generation endpoint protection.
CrowdStrike Falcon is a Cloud-based SaaS that offers vulnerability remediation tools. Falcon saves users the cost and effort of administering, maintaining, and updating on-premises software or equipment because it doesn't involve the installation of servers or controllers. The program makes mitigation strategies, blocking data tampering and monitoring harmful activity easier for network managers. Read CrowdStrike Falcon Reviews
Explore various CrowdStrike Falcon features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
CrowdStrike Falcon Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Emergents | 2024
Tools by GFI Software
GFI LanGuard offers one of the top vulnerability management tools. Leading patch management and network security scanner, GFI LanGuard serves as a virtual security advisor. GFI LanGuard provides risk analysis, gives users a complete picture of network configuration, and makes it easy to keep the network secure and compliant for users. Learn more about GFI LanGuard
Explore various GFI LanGuard features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Features
View all GFI LanGuard Features- Server Monitoring
- Network Diagnosis
- Dashboard
- Multi-Patch Deployments
- Vulnerability Scanning
- Automatic Scans
- Scheduled Deployment
- Baseline Manager
GFI LanGuard Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Emergents | 2024
Tools by Acunetix
An application security testing tool called Acunetix by Invicti Security assists small and mid-size businesses worldwide in taking charge of their web security. Acunetix is an automated vulnerability management platform for assessing the security of web applications and auditing web apps for exploitable flaws like SQL Injection and Cross-Site Scripting. Learn more about Acunetix
Explore various Acunetix features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Features
View all Acunetix Features- Vulnerability Protection
- Web Threat Management
- Vulnerability Assessment
- Asset Discovery
- Web Scanning
- Risk Management
- IOC Verification
- Asset Tagging
Acunetix Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Contenders | 2024
Tools by Tenable Network Security
Nessus is one of the best vulnerability management tools. It checks for security flaws in hardware, software, cloud services, operating systems, and other network resources. Professionals can access scan information with specifics and create an audit trail. Businesses can utilize data science and threat intelligence capabilities to identify critical issues. Read Tenable Nessus Reviews
Explore various Tenable Nessus features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Features
View all Tenable Nessus Features- Web Scanning
- Vulnerability Assessment
- Prioritization
- Policy Management
- Asset Discovery
- Network Scanning
Tenable Nessus Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Emergents | 2024
Tools by Tripwire
Tripwire is one of the best vulnerability management software that aids in monitoring and alerting specific file changes on a variety of platforms. Tripwire is a free software security and data integrity application. Tripwire Configuration Manager verifies that cloud accounts are secure and adhere to industry best practices by comparing them to CIS benchmarks. Learn more about Tripwire
Explore various Tripwire features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Features
View all Tripwire Features- Security Event Log
- Event Logs
- Server Monitoring
Tripwire Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Emergents | 2024
Tools by Automox
Automox is a patch management software devised for automating your cyber hygiene. It gives you absolute control over your infrastructure by resolving patch vulnerabilities, & maintaining configurations, besides ensuring the installation of the right software. Learn more about Automox
Explore various Automox features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Features
View all Automox Features- Network Wide Management
- Custom Patches
- Subscription Services
- Automatic Scans
- Scheduled Deployment
- Multi-Patch Deployments
Automox Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Contenders | 2024
Tools by Detectify
Detectify offers trustworthy vulnerability management tools. The Detectify solution encompasses security research automated into the solution. It helps translate the most recent security discoveries into vulnerability tests. Detectify collaborates precisely with the ethical hacking community. By doing so, businesses will gain access to cutting-edge security analysis and check their web application for vulnerabilities. Read Detectify Reviews
Explore various Detectify features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Features
View all Detectify Features- Asset Discovery
- Vulnerability Assessment
- Web Scanning
Detectify Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Emergents | 2024
Tools by Kenna Security
Kenna is a SaaS-based vulnerability management platform. It analyses risk accurately and prioritizes remedial actions before an attacker can take advantage of an organization's vulnerabilities. Kenna’s primary function is prioritizing the most critical vulnerabilities. Kenna is a fantastic tool for keeping software secure. It offers many security parameters and multiple security mechanism types. Learn more about Kenna
Explore various Kenna features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Features
View all Kenna Features- Web Scanning
- Asset Tagging
- Vulnerability Scanning
- Web Threat Management
- Multi-Patch Deployments
- Remote Protection
- Prioritization
- IP Protection
Kenna Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Contenders | 2024
Fastest and most accurate automated vulnerability
Based on the level of severity, the SanerNow vulnerability management tool evaluates and prioritizes the vulnerabilities. Businesses can also conveniently assess high-risk vulnerabilities. The SanerNow platform is used by IT and security teams to go beyond conventional vulnerability management processes and gain complete visibility and control over the organization's attack surface. Read SecPod's SanerNow Vulnerability Management Reviews
Explore various SecPod's SanerNow Vulnerability Management features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
- Diagnostic Tools
- Vulnerability Assessment
- Prioritization
- Whitelisting / Blacklisting
- Vulnerability Management
- Vulnerability Scanning
- Database Security Audit
- Real Time Monitoring
SecPod's SanerNow Vulnerability Management Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Emergents | 2024
Tools by Acunetix
Netsparker is a trustworthy vulnerability management software used by IT, security operations, and development teams. It is frequently used to identify current vulnerabilities in online applications and provides users with detailed findings that include recommendations for fixes. Netsparker aids in closing the cybersecurity skills gap and completely automates web security procedures. Learn more about Netsparker
Explore various Netsparker features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Features
View all Netsparker Features- Prioritization
- Asset Discovery
- Web Scanning
- Vulnerability Assessment
- Maintenance Scheduling
- Real Time Monitoring
- Database Security Audit
- IOC Verification
Netsparker Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Emergents | 2024
Tools by Intruder
Intruder is a cloud-based vulnerability remediation tool that looks for cyber security holes in digital infrastructure to avoid data breach. A user’s internal systems become the second most crucial priority after safeguarding any systems connected to the internet using External Vulnerability Scanner. Intruder is an online vulnerability scanner that recognizes cyber security flaws. Learn more about Intruder
Explore various Intruder features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Features
View all Intruder Features- Asset Tagging
- Two-Factor Authentication
- Patch Management
- Prioritization
- Vulnerability Scanning
- Vulnerability Assessment
- Asset Discovery
- Network Scanning
Pricing
Essential
$ 38
Per Month
Pro
$ 180
Per Month
Verified
$ 450
Per Month
Intruder Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Emergents | 2024
One-stop solution for all your security needs
AppTrana is a website and application security solution. It uses risk identification, scanning, pen testing, WAF, traffic monitoring, always-on security, and other techniques to aid enterprises in handling and maintaining cloud security. With the help of dashboards, this vulnerability tracking tool offers a 360-degree view of the user's application security. Read AppTrana Reviews
Explore various AppTrana features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Features
View all AppTrana Features- Web Traffic Reporting
- Threat Intelligence
- Vulnerability Protection
- Risk Assessment
- Real Time Monitoring
- Vulnerability Scanning
- Application Security
- Vulnerability Management
Pricing
Premium
$ 399
Per Month
Advance
$ 99
Per Month
Basic
$ 0
Forever
AppTrana Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Emergents | 2024
Tools by F-Secure Corporation
F-Secure offers top vulnerability management tools. It defends against ransomware by blocking unauthorized changes to data in significant directories like Documents and Pictures, similar to many security programs. F-Secure uses DeepGuard to detect access by dubious or harmful programs, unlike other security software that blocks all unfamiliar programs unless remove them. Learn more about F-Secure
Explore various F-Secure features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
F-Secure Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Emergents | 2024
Tools by Syxsense
Syxsense offers vulnerability management solutions for real-time vulnerability monitoring, detection, and intelligent automation for patch management, IT management, and security remediation in a single console. It aids in identifying vulnerabilities with the highest risk based on the business’s unique environment and pushes patches that will keep an organization safe and compliant. Learn more about Syxsense Manage
Explore various Syxsense Manage features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Features
View all Syxsense Manage Features- Automatic Scans
- Configuration Management
- Compliance Management
- Dashboard
- Custom Patches
- Vulnerability Scanning
- Audit Management
- Network Wide Management
Syxsense Manage Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Emergents | 2024
Tools by CA Technologies
Veracode Vulnerability Management is one of the best vulnerability management software. It offers an automated on-demand, application security testing service. Because Veracode is an on-demand service rather than an expensive on-premises solution, it is affordable. It identifies security flaws that may include malicious code as well as functional gaps that could result in security breaches. Learn more about Veracode Vulnerability Management
Explore various Veracode Vulnerability Management features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
- Web Scanning
- Vulnerability Assessment
- Policy Management
- Asset Discovery
Veracode Vulnerability Management Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Contenders | 2024
Worlds most powerful mobile security tool
Appknox is a widely used vulnerability management software. Appknox is an on-demand mobile application security platform that assists organizations in identifying and resolving security flaws. Appknox is very smooth in integrating with an existing security plan. Appknox is a potent plug-and-play mobile app security solution that can quickly identify dangers in apps. Read Appknox Reviews
Explore various Appknox features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Appknox Caters to
- StartUps
- SMBs
- Agencies
- Enterprises
Emergents | 2024
Tools by Greenbone Networks GmbH
OpenVAS offers reliable vulnerability remediation tools. It is suitable for high-level online threats, including cross-site scripting flaws, unauthorized file access, and known exploits in services it may access and on visible ports. The vulnerability scanner for OpenVAS recognizes the existence of an OpenVAS library and presents information on the vulnerabilities. Learn more about OpenVAS
Explore various OpenVAS features, compare the pricing plans, and unlock the potential of seamless operations by selecting the right software for your business.
Features
View all OpenVAS Features- Web Scanning
- Vulnerability Assessment
- Network Scanning
- Asset Discovery
- Prioritization
- Risk Management
- Asset Tagging
OpenVAS Caters to
- StartUps
- SMBs
- Agencies
- Enterprises

Organizations face an ever-growing array of cyber threats that can exploit vulnerabilities in their systems, networks, and applications. To counter these risks, Vulnerability Management Tools have emerged as crucial assets in the arsenal of modern cybersecurity.
These tools empower organizations to identify, assess, prioritize, and remediate vulnerabilities, allowing them to proactively fortify their defenses and minimize the potential impact of attacks. This discussion explores the pivotal role of Vulnerability Management Tools, delving into their features, benefits, challenges, and the dynamic trends shaping their evolution.
What are Vulnerability Management Tools?
Vulnerability management tools are essential cybersecurity solutions designed to identify, assess, prioritize, and mitigate vulnerabilities within an organization's digital infrastructure. These tools are critical in maintaining the security and integrity of systems, networks, and applications.
By continuously scanning and analyzing the various components of an IT environment, vulnerability management tools help identify potential security weaknesses, software flaws, misconfigurations, and outdated software versions that malicious actors could exploit.
Once vulnerabilities are detected, vulnerability management tools categorize and rank them based on severity, potential impact, and likelihood of exploitation. This enables security teams to allocate resources efficiently and first address the most critical vulnerabilities. Vulnerability management system facilitate remediation by providing guidance on fixing or mitigating vulnerabilities, often offering recommended solutions or patches.
How Do Vulnerability Management Tools Work?
Vulnerability tracking tools work systematically to identify and address security weaknesses within an organization's IT infrastructure. The process typically involves several key steps. First, the tool initiates scanning and examining systems, networks, applications, and other digital assets for potential vulnerabilities.
This can include software vulnerabilities, misconfigurations, weak passwords, and outdated software versions. Once vulnerabilities are identified, the tool then assesses their severity and potential impact on the organization's security posture. This involves assigning a risk score or severity level to each vulnerability.
After the assessment, vulnerability management tools prioritize the vulnerabilities based on their risk scores, helping security teams focus their efforts on addressing the most critical issues first. These tools often provide insights into the potential exploitation of vulnerabilities and the potential consequences if left unaddressed.
Next, vulnerability management tool assists in the remediation process by offering recommendations on mitigating or fixing the identified vulnerabilities. This could involve applying patches, changing configurations, updating software, or implementing security best practices.
Benefits of the Best Vulnerability Management System
Vulnerability Management System (VMS) fortifies an organization's security posture and ensures the swift resolution of vulnerabilities, bolstering its overall resilience against cyber threats. Here, we delve into the multifaceted benefits of an effective VMS, highlighting how it contributes to enhanced security and immediately fixes vulnerabilities.
-
Enhanced Security
At the heart of a VMS lies the ability to significantly enhance an organization's security measures. By continuously scanning and assessing various components of the IT environment, the system identifies vulnerabilities and weaknesses that could potentially be exploited by cybercriminals.
This proactive approach empowers security teams to avoid potential threats and address vulnerabilities before they can be weaponized. With real-time insights into security gaps, organizations can allocate resources more efficiently, strengthen their defenses, and prevent unauthorized access or data breaches. By regularly identifying and mitigating vulnerabilities, the VMS acts as a robust line of defense, safeguarding sensitive information and ensuring compliance with security standards.
-
Immediate Fix of Vulnerabilities
A distinguishing feature of a best-in-class vulnerability tracking software is its capacity to facilitate swift remediation of vulnerabilities. Upon detection, the system categorizes vulnerabilities based on their severity, allowing security teams to prioritize their response efforts. With recommended solutions, patches, or mitigation strategies provided by the VMS, organizations can rapidly take corrective action.
This agility is critical in preventing potential attacks, as cyber threats often evolve rapidly. Through automated processes and alerts, the VMS ensures that IT teams are promptly notified of vulnerabilities, enabling them to apply fixes and configurations in a timely manner. Consequently, this immediate responsiveness minimizes the window of opportunity for attackers and reduces the organization's exposure to security risks.
-
Quickly Respond to Threats
One of the primary advantages of an effective VMS is its ability to enable rapid responses to emerging threats. By continuously scanning networks, systems, and applications for vulnerabilities, the system identifies potential security gaps in real-time. This proactive approach ensures that security teams are immediately alerted to any vulnerabilities that malicious actors could exploit.
With timely notifications and prioritization based on the severity of the vulnerabilities, organizations can swiftly allocate resources to address high-risk issues. This agility in response significantly reduces the window of opportunity for attackers, preventing potential breaches and minimizing the impact of cyber incidents.
-
Gain Operational Efficiencies
The best vulnerability management system streamlines the vulnerability management process, increasing operational efficiencies. Manual vulnerability assessments and patching can be time-consuming and resource-intensive. However, a VMS automates these vulnerability management tasks, allowing security teams to focus on strategic activities rather than routine tasks.
Automated scans, vulnerability assessments, and patch deployments reduce human error, accelerate the identification of vulnerabilities, and optimize resource utilization. This efficiency translates into cost savings, as organizations can allocate their workforce to more value-added activities while maintaining a high-security level.
-
Automates Scanning and Patching
A hallmark feature of an optimal VMS is its capability to automate scanning and patching processes. The system schedules regular scans across the IT environment, identifying vulnerabilities and weak points. Additionally, it automates the deployment of patches and updates to remediate vulnerabilities swiftly.
This automation minimizes the manual effort required and ensures that critical vulnerabilities are addressed promptly, reducing the organization's exposure to potential threats. By keeping systems up to date-and patched, organizations can maintain a robust security posture while minimizing disruptions to ongoing operations.
-
Enhances Visibility and Reporting
A robust vulnerability management system offers enhanced visibility into an organization's security posture and vulnerability landscape. Comprehensive reporting and dashboards provide insights into the current state of vulnerabilities, their severity, and the progress of remediation efforts.
This transparency enables security teams, management, and stakeholders to make informed decisions based on accurate data. Additionally, detailed reports assist organizations in demonstrating compliance with security standards and regulations. The ability to visualize vulnerabilities and their mitigation status empowers organizations to track progress over time, allocate resources effectively, and communicate security efforts to relevant stakeholders.
Features of Best Vulnerability Management Tools
Vulnerability management tools offer a holistic approach to cybersecurity, equipping organizations with the means to proactively protect their systems, networks, and applications. Here, we delve into the detailed descriptions of each feature that vulnerability management tools bring to the table.

-
Vulnerability Scanning
Vulnerability scanning stands as a foundational feature of Vulnerability Management Tools. These tools conduct systematic scans of an organization's IT environment, examining systems, networks, and applications for potential security vulnerabilities.
By utilizing automated scans, organizations can quickly identify weaknesses, misconfigurations, and software flaws that malicious actors could exploit. This proactive approach allows security teams to avoid emerging threats and promptly address vulnerabilities before they are leveraged for attacks.
-
Risk Management
Vulnerability Management Tools offer robust risk management capabilities, enabling organizations to assess and prioritize vulnerabilities based on their potential impact and exploitability. These tools assign risk scores or severity levels to vulnerabilities, helping security teams focus their efforts on addressing the most critical risks. Through risk assessment, organizations can allocate resources efficiently and strategically to mitigate vulnerabilities that pose the greatest threat to their digital assets.
-
Patch Management
Patch management is a crucial component of the top vulnerability management tools. These tools assist organizations in keeping software and applications up to date by automating the deployment of patches and updates.
Organizations can close security gaps and prevent exploitation through known vulnerabilities by applying patches promptly. Patch management functionality streamlines the process, reducing the window of vulnerability and minimizing disruptions to ongoing operations.
-
Web Scanning
Web scanning is a specialized feature of Vulnerability Management Tools designed to assess the security of web applications and websites. These tools conduct comprehensive scans of web assets to identify vulnerabilities such as SQL injection, cross-site scripting (XSS), and other web-based threats. By evaluating the security of online platforms, organizations can protect user data, prevent unauthorized access, and maintain the trust of their digital audience.
-
Automated Asset Detection
Vulnerability Management Tools offer automated asset detection, enabling organizations to maintain an accurate inventory of their digital assets. These tools automatically discover and track devices, systems, and applications within the network. This feature assists organizations in identifying potential blind spots and ensuring that all components are scanned for vulnerabilities, thus enhancing overall security coverage.
-
Remediation Guidance
A hallmark feature of Vulnerability Management Tools is their provision of remediation guidance. Once vulnerabilities are identified, these tools offer recommendations, best practices, and step-by-step instructions on how to mitigate or fix the vulnerabilities. This guidance assists security teams in effectively addressing vulnerabilities, ensuring that they are resolved correctly and efficiently.
How to Choose the Right Vulnerability Management Software?
Selecting the right vulnerability management solution is a pivotal decision for organizations aiming to fortify their cybersecurity posture. With a multitude of options available, the process of choosing the ideal software requires careful consideration of various factors.
-
User Interface (UI)
An intuitive and user-friendly interface is paramount when choosing a vulnerability management software. The software's UI should facilitate easy navigation and efficient management of vulnerabilities. A well-designed UI streamlines the scanning process, vulnerability assessment, and remediation efforts.
Look for a software solution that presents information clearly, offers customizable dashboards, and provides meaningful visualizations. A user-friendly interface enhances the usability of the software, enabling security teams to swiftly identify and address vulnerabilities without facing unnecessary complexities.
-
Support
Effective customer support is a critical consideration when evaluating Vulnerability Management products. Inevitably, questions and issues will arise during the implementation and usage of the software. Ensure that vulnerability management system offers responsive and knowledgeable customer support channels. Look for email, phone, live chat, or an online knowledge base.
Additionally, assess whether the vendor provides training resources, documentation, and community forums to help users maximize the software's capabilities. Reliable support ensures that you can overcome challenges and make the most of the software's features.
-
Integrations
The ability of Vulnerability Management Software to integrate with your existing technology stack is paramount. Look for software that seamlessly integrates with the tools and systems you already use, such as Security Information and Event Management (SIEM) systems, endpoint protection solutions, and incident response platforms.
Integration capabilities enhance your organization's overall security ecosystem by enabling data sharing and streamlined workflows. This synergy between different security tools amplifies the effectiveness of your cybersecurity strategy.
-
Licenses and Cost
Understanding the licensing models and associated costs is crucial in selecting the right Vulnerability Management Software. Different vendors offer various licensing options, such as per-user, per-device, or subscription-based models. Assess your organization's needs and budget to determine which model aligns best.
Consider any hidden costs, such as maintenance, updates, and support. Evaluating the software's scalability is prudent – whether it can accommodate your organization's growth without significantly escalating costs.
Top 5 Vulnerability Management Tools Comparison
|
Name
|
Free Trial
|
Demo
|
Pricing
|
|---|---|---|---|
|
30 Days |
Yes |
On Request |
|
|
30 Days |
Yes |
Starting price at $2.19/asset/month |
|
|
14 Days |
Yes |
On Request |
|
|
7 Days |
Yes |
Starting price at $353.01/month |
|
|
7 Days |
Yes |
On Request |
Here is a list of the top five Vulnerability Management Tools, each distinguished by its unique features, user-centric design, and proven track record in enhancing cybersecurity measures.
1. Qualys Cloud Platform
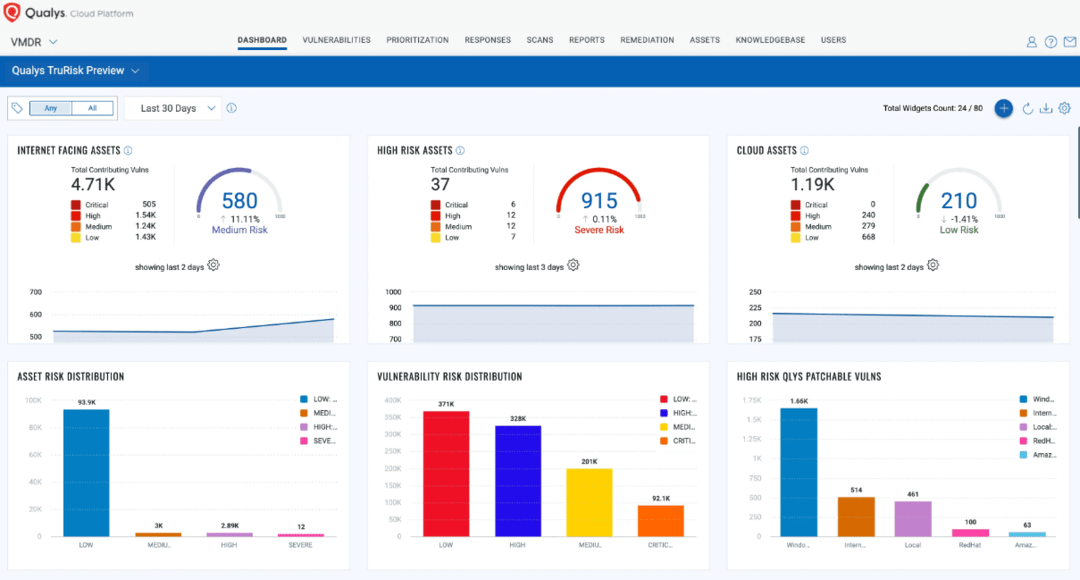
The Qualys Cloud Platform is a cutting-edge vulnerability management tool that offers a comprehensive and cloud-based solution for identifying, assessing, and mitigating vulnerabilities within an organization's digital infrastructure. With a user-friendly interface and robust features, the platform streamlines the vulnerability management process, providing real-time scanning, risk assessment, and remediation guidance.
Its integration capabilities ensure seamless connectivity with existing security tools, enhancing the overall cybersecurity ecosystem. Backed by responsive customer support and flexible licensing options, the Qualys Cloud Platform empowers organizations to proactively safeguard their systems, networks, and applications from potential threats, ultimately bolstering their security posture and digital resilience.
- Continuous vulnerability assessment
- Prioritization and risk analysis
- Remediation recommendations
- Cloud-based architecture
- User-friendly interface
- Continuous monitoring
- Asset discovery
- The software provides a control management feature.
- It has a unified dashboard for security posture.
- There is an ease of configuration.
- The reporting and alerting mechanism works very perfectly.
- The navigation is complex and involves a lot of pages to click through.
- The GUI could be a little less complicated.
- The software should have automated intelligence to identify and report common issues for a company.
Qualys Cloud Platform Pricing
- On Request
2. Rapid7 InsightVM
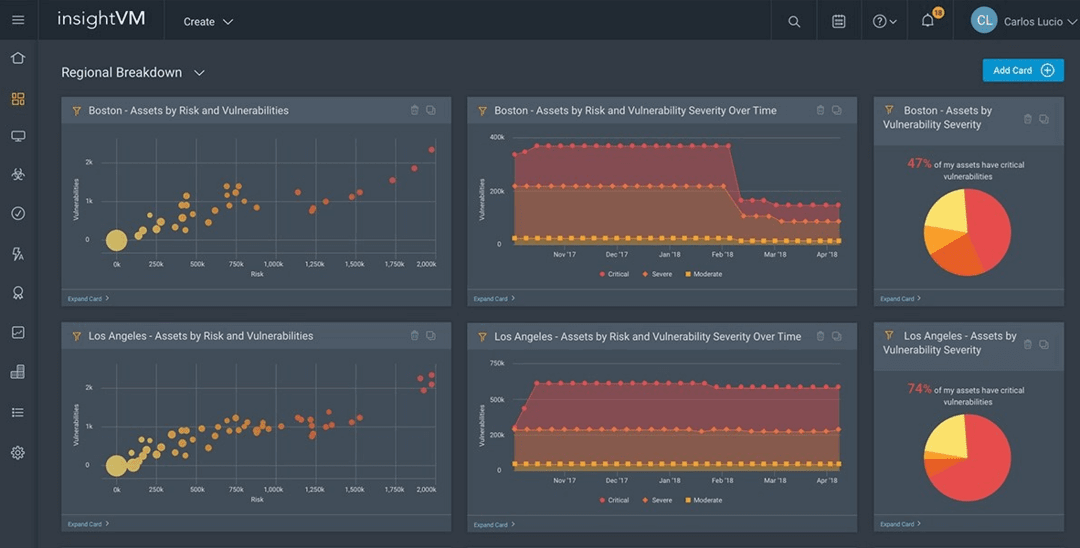
Rapid7 InsightVM is a distinguished vulnerability management system that combines advanced analytics with automation to enhance cybersecurity strategies. Offering contextual data-driven prioritization, the software aids organizations in focusing resources on critical vulnerabilities.
InsightVM's real-time alerts, comprehensive reporting, and intuitive user interface empower security teams to swiftly identify, assess, and address vulnerabilities across intricate IT environments. With its emphasis on risk mitigation and efficient remediation, Rapid7 InsightVM is a valuable tool for organizations seeking to proactively safeguard their digital assets.
- Contextual prioritization
- Real-time alerts
- Comprehensive vulnerability scanning
- Risk assessment
- Remediation guidance
- Automation capabilities
- Reporting and dashboards
- Integration Compatibility
- Continuous monitoring
- Cloud-based and on-premises options
- Compliance management
- Customizable reporting
- The queries against inventory are easy and useful.
- Most threats discovered have plenty of detail about the nature of the problem and how to mitigate it.
- Once the organization of the tool is understood, the operation is easy.
- The software's extensive features may come at a higher price point.
- While InsightVM integrates with various security solutions, the integration process might require additional configuration and setup, potentially causing some challenges.
Rapid7 InsightVM Pricing
- For 250 Assets, Per Asset: $2.19/month
- For 500 Assets, Per Asset: $1.93/month
- For 750 Assets, Per Asset: $1.79/month
- For 1000 Assets, Per Asset: $1.71/month
- For 1250 Assets, Per Asset: $1.62/month
3. Vulnerability Manager Plus
Vulnerability Manager Plus is a comprehensive vulnerability management tools designed to assist organizations in effectively managing and mitigating security vulnerabilities across their IT infrastructure. This tool offers a wide range of features to help identify, assess, prioritize, and remediate vulnerabilities in a streamlined and efficient manner. Providing a centralized vulnerability management platform helps organizations maintain a strong security posture and reduce the risk of cyberattacks.
- Risk assessment
- Remediation guidance
- Automation capabilities
- Integrations
- Compliance management
- Customizable reporting
- Reporting and dashboards
- All the patches are tested before being delivered.
- It's on the cloud, so the user doesn't need to maintain Hardware and Network.
- Easy-to-use UI and easy-to-understand dashboards.
- The software should provide more customization options.
- There should be a better reporting feature.
- Support needs to improve.
Vulnerability Manager Plus Pricing
- On Request
4. Tenable
Strong Vulnerability Management Software from Tenable places an emphasis on proactive risk management. Tenable helps businesses maintain a solid cybersecurity posture with a full range of services, such as vulnerability assessment, asset detection, and reporting. The software helps to secure digital assets by enabling security teams to quickly discover vulnerabilities and counter potential threats, thanks to its user-friendly interface and real-time warnings.
- Vulnerability assessment
- Asset discovery
- Real-time alerts
- Risk prioritization
- Comprehensive reporting
- Remediation guidance
- Integration Compatibility
- Cloud-based or on-premises
- Compliance support
- Continuous monitoring
- The software provides efficient and kind support.
- It updates apps with relative ease.
- It is simple to set up distribution servers.
- Reporting needs to improve in the software.
- Support needs to improve for better problem-solving of the clients.
- No prior information of client version update.
Tenable Pricing
- Tenable Nessus Professional for 1 year: $4,236.20
- Tenable Nessus Expert for 1 year: $6,242.20
- Tenable Vulnerability Management for 1 year: $2,684.50
- Tenable Web App Scanning for 1 year: $4,222.04
5. Acunetix
Acunetix is an industry-leading Vulnerability Management Software focused on web application security. This robust solution provides a comprehensive set of tools designed to identify, assess, and address vulnerabilities within web applications.
Through its advanced scanning techniques and in-depth analysis, Acunetix empowers organizations to proactively safeguard their online assets, detect potential security risks, and maintain the integrity of their web platforms. With a user-friendly interface and powerful reporting capabilities, Acunetix stands as a trusted ally for organizations seeking to enhance their cybersecurity posture in the ever-evolving digital landscape.
- Advanced web application scanning
- Comprehensive vulnerability assessment
- OWASP Top 10 coverage
- Automated crawling and scanning
- Remediation guidance
- Integration Compatibility
- API security
- Compliance support
- Advanced Reporting
- Integration of tools with different IDE is great.
- Easy to scan code and identify vulnerabilities.
- The dashboard is easy to customize.
- Configuration of DevSecOps can be improved for ease.
- Dashboard can have API integration.
- Broaden the scope of vulnerabilities.
Acunetix Pricing
- On Request
Challenges in Vulnerability Management System
Vulnerability management systems are not without challenges. Addressing these challenges is crucial for maintaining a robust security posture. Here, we delve into the detailed description of three significant challenges faced in Vulnerability Management Systems: incomplete asset inventory, prioritization of vulnerabilities, and overwhelming reports.

-
Incomplete Asset Inventory
One of the foremost challenges in Vulnerability Management Systems is maintaining a comprehensive and accurate inventory of assets. Organizations today possess diverse and dynamic IT environments, including servers, endpoints, applications, and network devices. Keeping track of these assets becomes complex due to frequent changes, shadow IT, and remote work arrangements.
Incomplete or outdated asset information hampers the effectiveness of vulnerability scans, as critical systems might be overlooked, leading to potential security gaps. Overcoming this challenge requires continuous asset discovery, automated inventory management, and integration with other IT management tools to ensure a holistic view of the organization's digital landscape.
-
Prioritization of Vulnerabilities
The sheer volume of vulnerabilities identified by scanning tools can overwhelm security teams, making it challenging to determine which vulnerabilities require immediate attention. Effective prioritization is crucial, as not all vulnerabilities pose the same level of risk.
Balancing factors such as severity, potential impact, and exploitability is intricate, and inaccurate prioritization can lead to resource inefficiency. Organizations need a clear methodology and criteria for ranking vulnerabilities, which can be complex due to the dynamic threat landscape. Implementing risk assessment frameworks, threat intelligence, and automation can aid in better prioritization, ensuring that high-risk vulnerabilities are addressed promptly.
-
Overwhelming Reports
While comprehensive reporting is crucial for vulnerability management, the volume and complexity of reports generated by scanning tools can overwhelm security teams. Lengthy reports with redundant information might hinder effective decision-making and resource allocation.
Additionally, translating technical details into actionable insights for non-technical stakeholders can be a challenge. To mitigate this, organizations need reporting tools that offer customization, clarity, and concise summaries. Automated data visualization, executive-level reporting, and targeted communication of findings can transform overwhelming reports into valuable resources for decision-makers.
Latest Trends in Vulnerability Management Tools
Keeping pace with the dynamic nature of digital threats, these tools are embracing innovative trends that enhance their capabilities and effectiveness. Below are the latest trends in vulnerability management tools -

-
Automation
Automation has become a cornerstone trend in Vulnerability Management solutions. Organizations are increasingly leveraging automation to streamline repetitive tasks, such as vulnerability scanning, assessment, and remediation.
By automating these processes, security teams can reduce human error, accelerate response times, and ensure that vulnerabilities are promptly addressed. Automation also enables quicker and more accurate risk prioritization, allowing organizations to focus on high-impact vulnerabilities.
-
Increased Focus on Cloud Security
As more organizations migrate their operations to the cloud, Vulnerability Management Tools are adapting to the unique challenges of cloud environments. These tools now provide specialized scanning and assessment for cloud infrastructure, applications, and services. Cloud-specific vulnerabilities and misconfigurations are given heightened attention, reflecting the shift towards a cloud-first approach and the need to secure virtualized resources effectively.
-
DevSecOps Integration
The integration of security into the DevOps process, known as DevSecOps, is a trending approach to vulnerability management. This methodology emphasizes collaboration between development, security, and operations teams throughout the software development lifecycle.
Vulnerability Management Tools adapt to this trend by integrating seamlessly into DevOps pipelines, facilitating early detection and remediation of vulnerabilities as code is developed and deployed.
-
Contextual Threat Intelligence
Vulnerability Management Tools incorporate contextual threat intelligence to enhance vulnerability assessment accuracy. By integrating external threat intelligence feeds, these tools gain insights into emerging threats and the likelihood of specific vulnerabilities being exploited. This contextual information enables organizations to prioritize vulnerabilities based on real-world risk, ensuring resources are allocated where they matter most.
-
Continuous Monitoring and Zero Trust Security
Vulnerability Management is moving towards continuous monitoring, where systems are under constant scrutiny to detect new vulnerabilities and threats. This trend aligns with the principles of zero trust security, which advocates for continuous verification and strict access controls. Vulnerability Management Tools now focus on monitoring for changes in the threat landscape, enhancing resilience against evolving cyber threats.
Conclusion
In the relentless pursuit of digital innovation, cybersecurity remains a paramount concern. Vulnerability Management Tools stand as a beacon of defense, offering organizations the means to stay vigilant against the ever-evolving landscape of cyber threats. Through automated scans, real-time alerts, risk prioritization, and actionable guidance, these tools enable organizations to identify vulnerabilities and fortify their digital assets.
While challenges such as incomplete asset inventories and overwhelming reports persist, advancements in automation, cloud security, and integration with DevSecOps practices promise to address these concerns. As the digital realm continues to expand, Vulnerability Management Tools will remain essential allies in the ongoing battle to safeguard sensitive data, maintain trust, and ensure the resilience of digital infrastructures.
FAQs
The cost of vulnerability management tools can vary widely based on factors such as the vendor, the scope of features, the size of the organization, and the deployment model (cloud-based or on-premises). Entry-level solutions start at a few thousand dollars annually, offering basic scanning and reporting capabilities.
More comprehensive and advanced tools with additional features, integrations, and support can range from $10,000 to 100k dollars per year. Custom pricing models are often employed for larger enterprises with complex requirements. It's important to consider the specific needs of your organization and the value the tool brings in terms of enhanced security and risk mitigation when evaluating costs.
Evaluating a vulnerability management tool involves considering several key factors. First, assess its scanning capabilities – ensure it covers your technology stack comprehensively. Evaluate the tool's accuracy in identifying and prioritizing vulnerabilities based on severity and potential impact. Integration capabilities are crucial; check if it can seamlessly work with your existing security solutions.
The user interface should be intuitive, aiding efficient navigation and reporting. Assess the vendor's reputation, customer support quality, and training resources. Additionally, examine the tool's scalability to accommodate your organization's growth. Finally, factor in the cost and licensing model, ensuring it aligns with your budget and provides value in enhancing your cybersecurity efforts.
Vulnerability management software and antivirus software serve distinct but complementary roles in cybersecurity. Vulnerability management focuses on identifying and addressing security vulnerabilities within systems, networks, and applications to prevent potential exploits. It conducts scans, prioritizes risks, and offers guidance for remediation.
On the other hand, antivirus software primarily targets known malware and viruses, detecting and removing malicious code to prevent infections. While vulnerability management emphasizes proactive risk mitigation through patching and configuration management, antivirus tools primarily focus on reactive threat detection and removal. Both are essential components of a comprehensive cybersecurity strategy, addressing different aspects of the threat landscape.
Vulnerability assessment and vulnerability management tools are closely related but serve distinct purposes. Vulnerability assessment tools are designed to scan systems, networks, and applications to identify potential vulnerabilities. They provide insights into the security gaps that could be exploited by attackers. On the other hand, vulnerability management tools encompass a broader scope.
They not only identify vulnerabilities but also prioritize them based on factors like severity and potential impact. These tools offer guidance for remediation, automation of patch deployment, and continuous monitoring to ensure that vulnerabilities are addressed effectively. In essence, vulnerability assessment tools pinpoint vulnerabilities, while vulnerability management tools encompass the entire lifecycle of identifying, prioritizing, and mitigating those vulnerabilities.





















