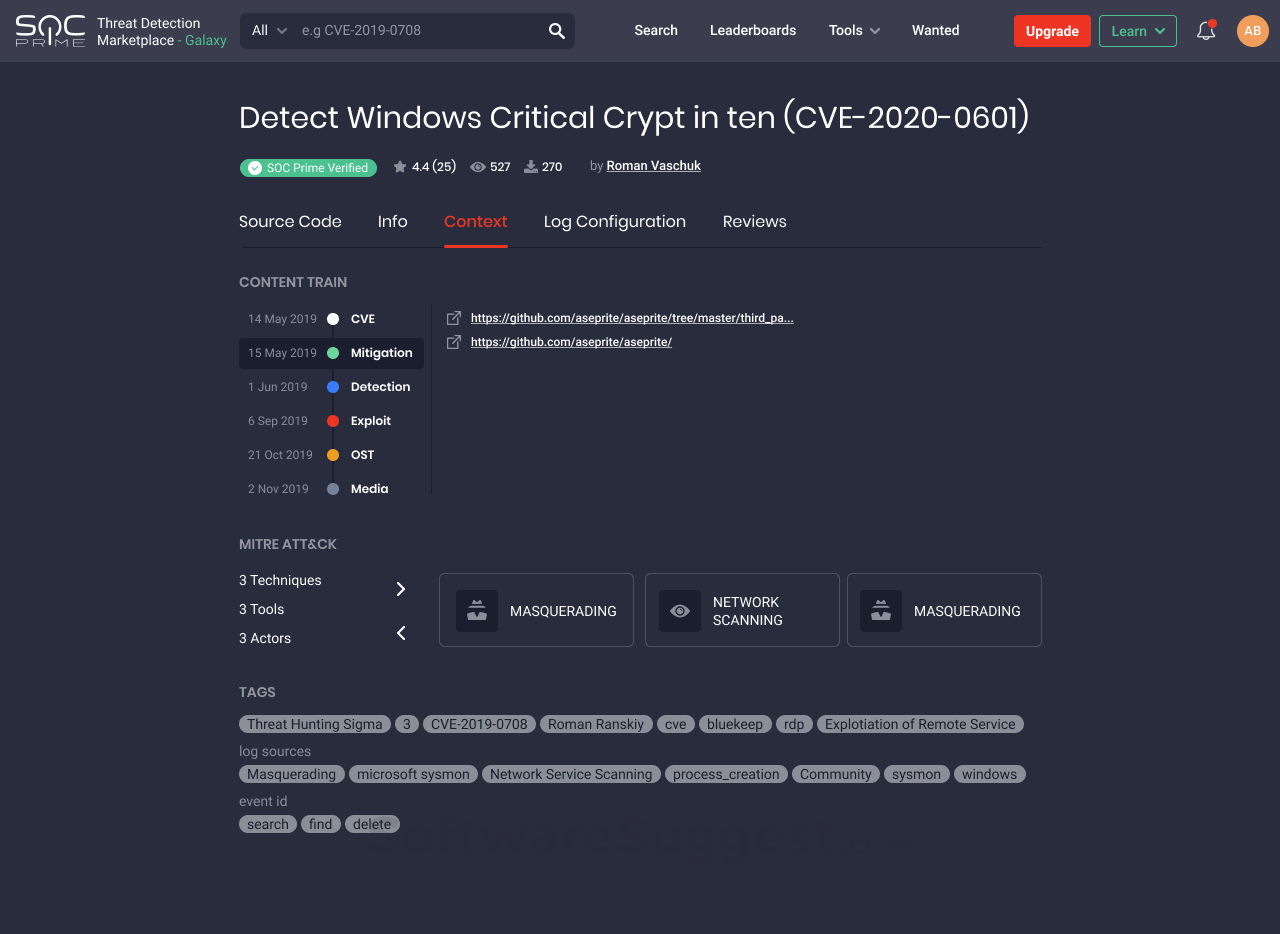

What is SOC Prime Threat Detection Marketplace?
SOC Prime Threat Detection Marketplace (TDM) is a SaaS cross-platform content community daring to integrate versatile cybersecurity components into one coherent system. We help security professionals to detect and respond to cyber threats.
SOC Prime Threat Detection Marketplace Starting Price

Our Awards and Recognition
Talk with a software expert for free. Get a list of software that's great for you in less than 10 minutes.
Key Features of SOC Prime Threat Detection Marketplace
Here are the powerful features that make SOC Prime Threat Detection Marketplace stand out from the competition. Packed with innovative tools and advanced functionalities, this software offers a range of benefits.
- Behavioral Analytics
- Compliance Reporting
- Endpoint Management
- File Integrity Monitoring
- Forensic Analysis
- Log Management
- Network Monitoring
- Real Time Monitoring
- Threat Intelligence
- User Activity Monitoring
- Activity Log
- AI / Machine Learning
- AI Security
- Anti Virus
- Anti-Spyware
- Antivirus
- Application Security
- Asset Discovery
- Asset Tagging
- Audit Trail
- Behavioral Analytics
- Biometric
- Blue Team Tools
- Compliance Management
- Compliance Reporting
- Content Caching
- Access control and identity management
- API Security
- API security and management
- Application security and firewalling
- Attack Surface Management
- Cloud access governance
- Cloud Compliance
- Cloud compliance management
- Cloud Detection and Response (CDR)
- Cloud Infrastructure Entitlement Management (CIEM)
- Cloud security
- Cloud Security Posture Management (CSPM)
- Cloud workload protection
- Cloud-Native Application Protection Platforms (CNAPP)
- Computer Security
- Container security
SOC Prime Threat Detection Marketplace Specifications
Get a closer look at the technical specifications and system requirements for SOC Prime Threat Detection Marketplace. Find out if it's compatible with your operating system and other software.
- Elactic
- Microsoft Azure Sentinel
- Sumo Logic
- RSA NetWitness
- LogPoint
- Humio
- QRadar
- ArcSight
- Graylog
- Regex Grep
- Microsoft Defender ATP
- Carbon Black
- CrowdStrike
- Qualys
- Corelight/Zeek
- Splunk
- Microsoft PowerShell
SOC Prime Threat Detection Marketplace Description
Here's the comprehensive description of SOC Prime Threat Detection Marketplace. Gain a brief understanding of its unique features and exceptional benefits.
SOC Prime Threat Detection Marketplace (TDM) is a SaaS cross-platform content community daring to integrate versatile cybersecurity components into one coherent system. We help security professionals to detect and respond to cyber threats at the earliest stages of the attack lifecycle, enhancing the capabilities and increasing ROI for the most popular SIEM, EDR, NSM and SOAR tools. Together we continuously deliver rules, parsers, and machine learning models covering the latest threats, attacker tactics, techniques, and procedures (TTP), cloud security monitoring, and proactive exploit detection.
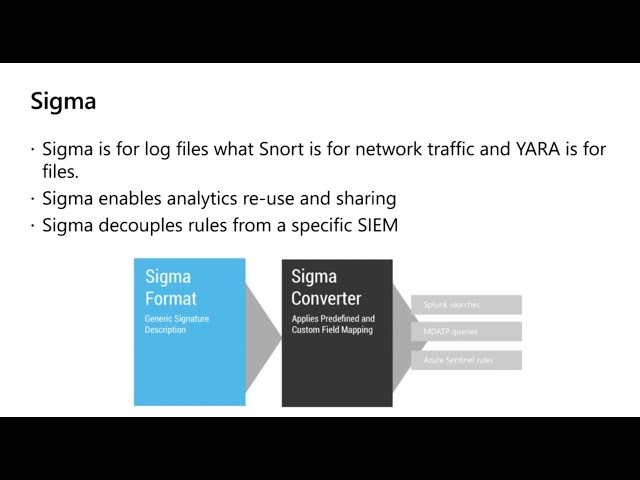
All types of threat detection content offered by the TDM community — over 55k SIEM and EDR rules, search queries, Snort and YARA rules and more — are being developed to fit various environments. SOC Prime TDM delivers content using Sigma, a generic and open SIEM signature format, which can be applied across various platforms. Currently, the SOC Prime TDM community provides access to 15+ supported platforms including:
SIEMs: Microsoft Azure Sentinel, Sumo Logic, Humio, Elastic Stack, Splunk, ArcSight, LogPoint, QRadar, and Graylog
EDRs: Microsoft Defender ATP, Carbon Black, CrowdStrike, Qualys
NSM and NTA solutions: Corelight / Zeek
SOC Prime makes threat detection easier and much more accessible. The company’s core product, Threat Detection Marketplace (TDM) is a SaaS content platform and community that has taken a challenge-driven approach to integrate multiple cybersecurity components into one coherent system. Leveraging TDM capabilities, cybersecurity specialists can maximize their team productivity and help their companies succeed in:
- Proactive deployment of threat detection capabilities
- Enhanced ROI of SIEM, EDR, NSM and SOAR investments
- Reduced Mean Time to Detect (MTTD) metrics
The SOC Prime TDM community offers a wealth of threat detection content — 55k+ SIEM and EDR rules, search queries, Snort and YARA rules and more content types that can be adjusted to various environments. The platform delivers content using Sigma, a generic open-source rule format for multiple SIEM systems. Giving preference to this signature format adds to the company’s flexibility since Sigma is becoming a commonly used method to build content and can be applied across various solutions. With SOC Prime TDM and its powerful analytical capabilities, companies can detect and respond to cyber threats at the initial stages of the attack lifecycle. More than 94% of the TDM content is mapped directly to the MITRE ATT&CK® framework that allows organizations to implement content perfectly fitting their unique threat profile.
TDM is a content platform with a strong sense of community that promotes global collaboration with threat hunters who can develop their own content, share it with the TDM community, and get paid for their contribution. Participation in the related Threat Bounty project, which has been thriving since May 2019, offers a brilliant opportunity to seasoned and promising developers to contribute to the global community evolving cyber defence through collaboration.
SOC Prime Threat Detection Marketplace Resources

SOC Prime Threat Detection Marketplace Slideshare
SOC Prime Threat Detection Marketplace Videos
SOC Prime Threat Detection Marketplace Reviews (0)
No reviews yet. Rate this app or be the first to review.
Write a ReviewAlternatives of SOC Prime Threat Detection Marketplace
Explore alternative software options that can fulfill similar requirements as SOC Prime Threat Detection Marketplace. Evaluate their features, pricing, and user feedback to find the perfect fit for your needs.
SOC Prime Threat Detection Marketplace FAQs
What apps do SOC Prime Threat Detection Marketplace integrate with?
SOC Prime Threat Detection Marketplace integrates with various apps:
- Elactic
- Microsoft Azure Sentinel
- Sumo Logic
- RSA NetWitness
- LogPoint
- Humio
- QRadar
- ArcSight
- Graylog
- Regex Grep
- Microsoft Defender ATP
- Carbon Black
- CrowdStrike
- Qualys
- Corelight/Zeek
- Splunk
- Microsoft PowerShell
What are the top 5 features for SOC Prime Threat Detection Marketplace?
The top 5 features for SOC Prime Threat Detection Marketplace are:
- Real Time Monitoring
- Compliance Management
- Incident Management
- Event Logs
- Event-Based Notifications
What type of customer support is available from SOC Prime Threat Detection Marketplace?
The available support which SOC Prime Threat Detection Marketplace provides is:
- Phone
- Live support
- Tickets
- Training