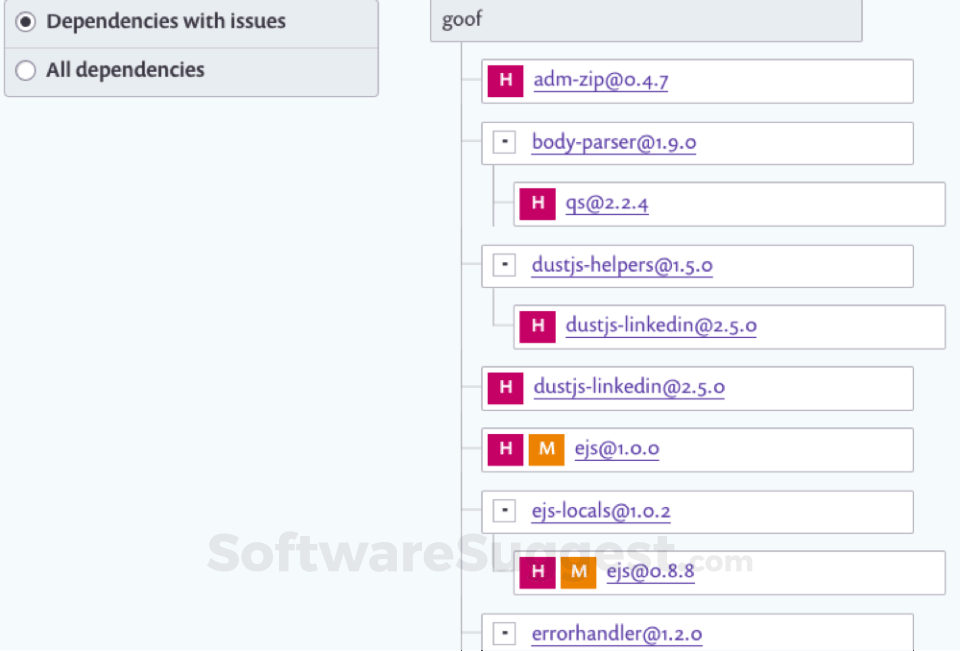
What is Snyk?
Snyk is a fully featured Security Management Software designed to serve Agencies, Startups. Snyk provides end-to-end solutions designed for Web App. This online Security Management system offers Prioritization, Patch Management, Risk Management, Vulnerability Assessment, Asset Discovery at one place.
Snyk Starting Price
$ 0/Per Month

Our Awards and Recognition
Talk with a software expert for free. Get a list of software that's great for you in less than 10 minutes.
Key Features of Snyk
Here are the powerful features that make Snyk stand out from the competition. Packed with innovative tools and advanced functionalities, this software offers a range of benefits.
- Access control
- Activity Log
- Activity Monitoring
- Advanced Firewall
- AI / Machine Learning
- Anonymous Browsing
- Anti Spam
- Anti Virus
- Application Access Control
- Application Security
- Archiving
- Asset Discovery
- Asset Tagging
- Audit Trail
- Audit Trails
- Availability Testing
- Activity Log
- AI / Machine Learning
- AI Security
- Anti Virus
- Anti-Spyware
- Antivirus
- Application Security
- Asset Discovery
- Asset Tagging
- Audit Trail
- Behavioral Analytics
- Biometric
- Blue Team Tools
- Compliance Management
- Compliance Reporting
- Content Caching
- Asset Discovery
- Asset Tagging
- Asset Discovery
- Asset Tagging
- Compliance Reporting
- Compression
- Continuous Backup
- Database Security Audit
- Diagnostic Tools
- IOC Verification
- Local Server Options
- Maintenance Scheduling
- Multiple System Support
- Network Scanning
- Patch Management
- PCI Assessment
- Access control
- Application Security
- Application Security Orchestration and Correlation (ASOC)
- Application Server
- Applied Behavior Analysis (ABA)
- Authentication and Authorization
- Code Review
- Compliance monitoring
- Content Security Policy (CSP)
- Cross-Site Request Forgery (CSRF) Prevention
- Cross-Site Scripting (XSS) Prevention
- Data Encryption
- DevSecOps
- Dynamic Application Security Testing (DAST)
- Electronic medical records (EMR)
- Error handling and logging
- Analysis of Code Structure and Dependencies
- API and Library Scanning
- Automated Vulnerability Detection
- Code Review Workflow Management
- Code Scanning
- Compliance Checking
- Compliance with Industry Standards
- Continuous Integration (CI) and Continuous Deployment (CD) Integration
- Cross-Language Support
- Customizable Rule Sets
- Data Flow Analysis
- Detection of Coding Errors and Bugs
- Detection of Insecure Coding Practices
- Detection of Security Misconfigurations
- Extensibility and Plugin Support
- False Positive Reduction
Snyk Pricing
Here are the pricing plans for Snyk. Choose the plan that best fits your requirements and budget. Get Detailed Snyk pricing as per your requirements.
- Unlimited tests on open-source projects
- 200 tests on private projects, up to 100 container tests.
- Github.com, Bitbucket Cloud, Azure Repos & Gitlab.com (Cloud Git) Integration
- Remediation for open-source projects
- CI/CD pipeline integration
- Continuous monitoring
- Unlimited application dependency tests
- Reports
- Bill of Materials
- Licenses
- Rich API
- Unlimited container tests (optional add-on)
- On Prem Git (GitHub, Bitbucket, GitLab)
- Single Sign On (SSO)
- Teams & Groups
- Jira integration
- Service Accounts
- Unlimited container tests (optional add-on)
Snyk Specifications
Get a closer look at the technical specifications and system requirements for Snyk. Find out if it's compatible with your operating system and other software.
Snyk Comparisons
Compare Snyk with other similar options available in Security Management Software. Explore the key differences to see why it's the top choice for businesses and individuals.

Snyk Videos
Snyk Reviews (0)
No reviews yet. Rate this app or be the first to review.
Write a ReviewAlternatives of Snyk
Explore alternative software options that can fulfill similar requirements as Snyk. Evaluate their features, pricing, and user feedback to find the perfect fit for your needs.
Snyk FAQs
How much does Snyk cost?
The starting price of Snyk is ₹ 0/Per Month. It has different pricing plans:
- Free : ₹ 0/Per Month
- Standard : ₹ 43128/Per Month
- Pro : ₹ 119448/Per Month
The details of Snyk’s free trial have not been shared by the vendor.
What are the top 5 features for Snyk?
The top 5 features for Snyk are:
- Risk Management
- Policy Management
- Vulnerability Scanning
- Prioritization
- Patch Management
What type of customer support is available from Snyk?
The available support which Snyk provides is: