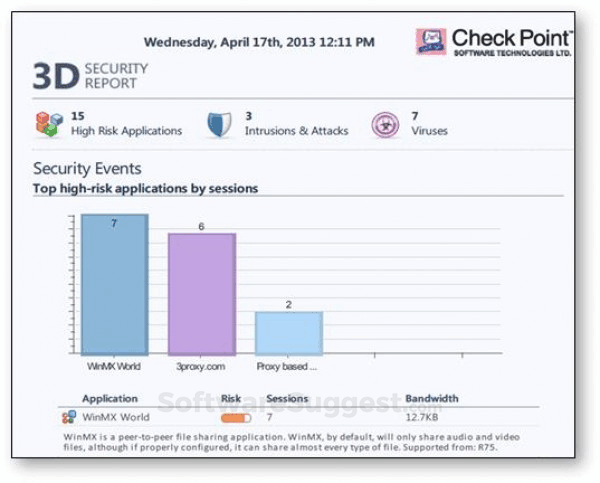
What is Check Point?
Check Point’s Secure Knowledge is a safe knowledge base solution to solve technical problems for Check Point products. It is a customizable software with intuitive interface. It is maintained by a group of qualified technicians and contains all the common question and answers that are submitted to Check Point Tac.
Check Point Starting Price

Our Awards and Recognition
Talk with a software expert for free. Get a list of software that's great for you in less than 10 minutes.
Key Features of Check Point
Here are the powerful features that make Check Point stand out from the competition. Packed with innovative tools and advanced functionalities, this software offers a range of benefits.
- Activity / News Feed
- Adaptive Learning
- Alerts / Escalation
- Analytics/ROI Tracking
- Approval Process Control
- Archiving & Retention
- Artwork Management
- Asset Management
- Asynchronous Learning
- Audit Trail
- Automated Review & Approval
- Benchmarking
- Blended Learning
- Blogs
- Brainstorming
- Built-In Course Authoring
- Access control
- Activity Log
- Activity Monitoring
- Advanced Firewall
- AI / Machine Learning
- Anonymous Browsing
- Anti Spam
- Anti Virus
- Application Access Control
- Application Security
- Archiving
- Asset Discovery
- Asset Tagging
- Audit Trail
- Audit Trails
- Availability Testing
- Audit Trails
- Automated Review & Approval
- Best Practices Library
- Billing & Invoicing
- Broker / Agent Portal
- Cancellation Tracking
- Claims Management
- Claims Tracking
- Collaboration
- Compliance Management
- Consent Management
- Content Management
- Dashboard
- Document Management
- Higher Education
- Insurance Rating
- Activity Log
- AI / Machine Learning
- AI Security
- Anti Virus
- Anti-Spyware
- Antivirus
- Application Security
- Asset Discovery
- Asset Tagging
- Audit Trail
- Behavioral Analytics
- Biometric
- Blue Team Tools
- Compliance Management
- Compliance Reporting
- Content Caching
- Cloud Protection
- Compliance Reporting
- Cybersecurity
- Dashboard
- Data Classification
- Data Containerization
- Data Discovery
- Data loss prevention
- Device Control
- Device management
- Email Security
- Endpoint Detection and Response (EDR)
- Endpoint protection
- False Positive Remediation
- Incident Management
- Insider Threat Management
Check Point Specifications
Get a closer look at the technical specifications and system requirements for Check Point. Find out if it's compatible with your operating system and other software.
Check Point Comparisons
Compare Check Point with other similar options available in Knowledge Management System. Explore the key differences to see why it's the top choice for businesses and individuals.

Check Point Slideshare
Check Point Videos
Check Point Reviews (0)
No reviews yet. Rate this app or be the first to review.
Write a ReviewAlternatives of Check Point
Explore alternative software options that can fulfill similar requirements as Check Point. Evaluate their features, pricing, and user feedback to find the perfect fit for your needs.
Check Point FAQs
What are the top 5 features for Check Point?
The top 5 features for Check Point are:
- Collaboration
- Data Management
- Discussion Boards
- Self Service Portal
- Document Management
What type of customer support is available from Check Point?
The available support which Check Point provides is:
Where is the headquarters/company of Check Point located?
The headquarters/company of Check Point is located at San Carlos.